42 isilon antivirus best practices
FAQ: What is ISILON OneFS and does Informatica DEI support this filesystem? OneFS combines the 3 layers of traditional storage architectures—the file system, volume manager, and data protection into one unified software layer creating a single intelligent file system that spans all nodes within a cluster. Features of the EMC Isilon OneFS Operating System: Designed for Big Data. Simplicity, Speed, and Scalability. Dell EMC E20-555 Real Practice Exam - Vendor Dell EMC Exam... Dell EMC E20-020 Exam Best Practice Questions. test_prep. 3. h17955-dell-emc-isilon-antivirus-solutions.pdf. University of Science and Technology HOUARI BOUMEDIENE ALGERIA ... University of Science and Technology HOUARI BOUMEDIENE ALGERIA • CIS MISC. h17955-dell-emc-isilon-antivirus-solutions.pdf. 16. E20-526 Exam Dumps V9.02 - DumpsBase Free ...
Isilon (NAS) | Configuration Best Practices—Dell EMC Storage with the ... The Isilon system uses the Reed-Solomon algorithm for N+M protection with Forward Error Correction (FEC). Protection is applied at the file level, enabling the cluster to recover data quickly and efficiently. Nodes, directories, and other metadata are protected at the same or a higher level as the data blocks they reference.

Isilon antivirus best practices
Eyeglass and PowerScale Failover Best Practices - superna Best Practice General: Eyeglass - We recommend DFS mode for SMB share protection and DR Eyeglass - We recommend Access Zone Failover when NFS and SMB data needs to failover together Eyeglass - We recommend syncIQ policy mode failover for customers with small numbers of NFS exports and hosts for automation PowerScale and Isilon technical white papers and videos Symptoms. We have moved! Visit our new location on the Dell Technologies Info Hub where you can find the latest technical content for Dell PowerScale (Isilon). For detailed documentation about how to install, configure, and manage your PowerScale OneFS system, visit the PowerScale OneFS Info Hubs. h12428 Wp Best Practice Guide Isilon File System Auditing Best Practices for Isilon Content Best Practices Guide Abstract This white paper outlines best practices to configure a File System Audit solution in an SMB environment with EMC Isilon, EMC Common Event Enabler (CEE), and Varonis DatAdvantage. April 2014 FILE SYSTEM AUDITING WITH EMC ISILON, EMC COMMON EVENT ENABLER, AND VARONIS DATADVANTAGE 2
Isilon antivirus best practices. PDF Dell EMC Isilon Ransomware Workshop - Varonis Collect, create, analyze metadata from Dell EMC Isilon Analyze behavior, profile key accounts, and develop a baseline for each user and device Identify unusual behavior with machine learning algorithms and behavioral rule sets Alert on behavioral anomalies and suspicious activity How it works 22 Access Activity Permissions Content Discovery PDF Dell EMC Networking with Isilon Front-End Deployment and Best Practices ... 6 Dell EMC Networking with Isilon Front-End Deployment and Best Practices Guide | version 1.0 However, Dell EMC Networking's legacy OS9 is still prevalent in the industry and supported on a large cross-section of the currently-shipping portfolio. This document encompasses the use of both operating systems within the same network architecture. Migrate Data off of the Isilon (General Data Storage) Disable antivirus The Active Directory User for transfer should be in the access control list for both the source and destination shares Test syncs should be done to verify speeds Ideally should be dedicated to the copying and not a server used for production More than one server could be used for larger migrations Access zones best practices - doc.isilon.com Access zones best practices. You can avoid configuration problems on the Isilon cluster when creating access zones by following best practices guidelines. Access zones on a SyncIQ secondary cluster. You can create access zones on a SyncIQ secondary cluster used for backup and disaster recovery, with some limitations. Access zone limits
PDF Isilon Design and Considerations for SMB - Dell USA SMB design considerations and common practices H17463.1 1 SMB design considerations and common practices 1.1 SMB protocol introduction The SMB protocol is a network file sharing protocol, and as implemented in Microsoft Windows® is known as the Microsoft SMB protocol. The set of message packets that defines a particular version of the protocol is Isilon Antivirus Best Practices | PDF | Antivirus Software - Scribd Best Practice Recommendations for Capacity and Performance Abstract This white paper provides technical information to consider when planning an EMC Isilon Scale Out storage solution that requires antivirus capabilities and using the Internet Content Adaptation Protocol (ICAP) to manage the scanning with an off-box scan PDF Isilon IQ and VMware vSphere 4 An Isilon cluster can survive an unprecedented four (N+4) simultaneous failures of either entire nodes or drives, regardless of the capacity of the drive. In contrast traditional systems can at best sustain only two drive or system failures with traditional RAID protection (e.g. RAID6, RAID DP, N+2, mirroring). FlexProtect™ Virtual Hot Spare Best Practice Guide list for Trend Micro products This article contains a list of the most recent Best Practice Guides for Trend Micro's major products. Product. Link. Apex Central. Apex Central 2019 Best Practice Guide. Apex One. Apex One as a Service. Best practices in configuring Apex One for malware protection. Cloud App Security.
LogicMonitor Security Best Practices | LogicMonitor Set strong passwords for administrative accounts Change other default passwords as applicable Disable guest accounts and unnecessary network services Protect the system from the public internet using either a host-based or network-based firewall Stay current with vendor-provided security patches Anti-Malware Exemptions Recommended antivirus exclusions for Hyper-V hosts - Windows Server ... You may have antivirus software installed and running on a Hyper-V host. For optimal operation of Hyper-V and the running virtual machines, you should configure several exclusions and options. These configurations will help avoid issues, such as those that are described in the following article: Best Practices Guide for Maintaining Enough Free Space on Isilon ... Transcript. BEST PRACTICES GUIDE FOR MAINTAINING ENOUGH FREE SPACE ON ISILON CLUSTERS AND POOLS October 31, 2016. Abstract Consuming all available storage space on an Isilon cluster or pool can have a major impact on your workflow and the cluster's data protection capabilities. However, it is one of the easiest problems to avoid. Free Isilon Fundamentals 2017 e-Learning - Intelligent Systems Monitoring This Isilon Fundamentals 2017 course provides an introduction and basic understanding of the Dell EMC Isilon scale-out Storage Platform. It includes an overview of the Isilon architecture, features, and functionality. This course is intended for professionals who will be designing, deploying, managing and supporting Isilon storage platforms.
PDF Dell EMC Isilon: Antivirus Solutions - Dell Technologies Antivirus policy scanning Using the OneFS Job Engine, you can create antivirus scanning policies that send files from a specified directory to be scanned. Antivirus policies can be run manually at any time or configured to run according to a schedule. Individual file scanning This type sends a specific file to the ICAP server to run the scan.
Planning for an Azure File Sync deployment | Microsoft Learn It's a best practice to keep the number of items per sync scope low. That's an important factor to consider in your mapping of folders to Azure file shares. Azure File Sync is tested with 100 million items (files and folders) per share. But it's often best to keep the number of items below 20 million or 30 million in a single share.
PDF BEST PRACTICES FOR DATA REPLICATION WITH EMC ISILON SYNCIQ - Google Groups features and benefits of EMC Isilon SynclQ software and describes how SyncIQ enables enterprises to flexibly manage and automate data replication between two Isilon clusters. This paper also describes best practices and use cases to maximize the benefits of cluster-to-cluster replication. November 2012 . BEST PRACTICES FOR DATA REPLICATION
PDF EMC® Avamar® 7.1 Operational Best Practices Server Management tab.....32 Backup/Maintenance windows.....38
Isilon multiprotocol best practices - gmidyr.tonoko.info BEST PRACTICES FOR DATA REPLICATION. that Isilon is a multiprotocol filesystem and supports multiple auth providers the best way to control data access is through filesystem permissions Isilon Local User and Group for Proxy Authentication Setting March 30th, 2019 - RPO Reporting and Trending Feature Guide Role Based Access Controls RBAC Configure.
PDF ANTIVIRUS SOLUTIONS WITH EMC ISILON SCALE-OUT NAS - Dell There are two methods that EMC Isilon storage clusters can use to scan files for threats. One is called "on access" in which a file is vectored to the ICAP antivirus scan engine when the file is requested by the end user. It is scanned and appropriate actions are taken. The other method is via policy defined on the storage array itself.
PowerScale: AntiVirus Solutions | Dell Technologies Info Hub This document provides best practices for planning a Dell EMC Isilon scale-out storage solution that requires antivirus capabilities as well as the Internet Content Adaptation Protocol (ICAP) to manage scanning with an off-box scan engine. Download PDF
Access zones best practices - Dell An access zone is limited to a single Active Directory provider; however, OneFS allows multiple LDAP, NIS, and file authentication providers in each access zone. It is recommended that you assign only one type of each provider per access zone in order to simplify administration. Avoid overlapping UID or GID ranges for authentication providers ...
PDF NTP Software QFS® for Isilon® - DefendX To prepare the EMC Isilon, the following needs to be taken into consideration: 1. Each Isilon managed by NTP Software QFS must join the same domain as the QFS machine. 2. The logon account used to register with the EMC Isilon (the account that will be assigned to the QFS connector service) needs to be a member of the Isilon's local
Isilon multiprotocol best practices - nknwng.preservonsdemain.fr EMC WHITE PAPER EMC ISILON BEST PRACTICES FOR HADOOP DATA STORAGE ABSTRACT This paper describes the best practices for setting up and managing the HDFS service on an EMC Isilon cluster to optimize data storage for Hadoop analytics. This paper covers OneFS 7.2 or later. January 2015.. "/>. unity clipping shader valorant hit registration 2022
PDF SyncIQ Best Practices Guide - Google Groups benefits as well as best practices and use cases to help you maximize the benefits of cluster-to-cluster replication. SyncIQ enables you to flexibly manage and automate data replication between two Isilon IQ clusters. The SyncIQ module can copy data from one Isilon cluster to another, or synchronize data by replicating files from a source cluster
h12428 Wp Best Practice Guide Isilon File System Auditing Best Practices for Isilon Content Best Practices Guide Abstract This white paper outlines best practices to configure a File System Audit solution in an SMB environment with EMC Isilon, EMC Common Event Enabler (CEE), and Varonis DatAdvantage. April 2014 FILE SYSTEM AUDITING WITH EMC ISILON, EMC COMMON EVENT ENABLER, AND VARONIS DATADVANTAGE 2
PowerScale and Isilon technical white papers and videos Symptoms. We have moved! Visit our new location on the Dell Technologies Info Hub where you can find the latest technical content for Dell PowerScale (Isilon). For detailed documentation about how to install, configure, and manage your PowerScale OneFS system, visit the PowerScale OneFS Info Hubs.
Eyeglass and PowerScale Failover Best Practices - superna Best Practice General: Eyeglass - We recommend DFS mode for SMB share protection and DR Eyeglass - We recommend Access Zone Failover when NFS and SMB data needs to failover together Eyeglass - We recommend syncIQ policy mode failover for customers with small numbers of NFS exports and hosts for automation
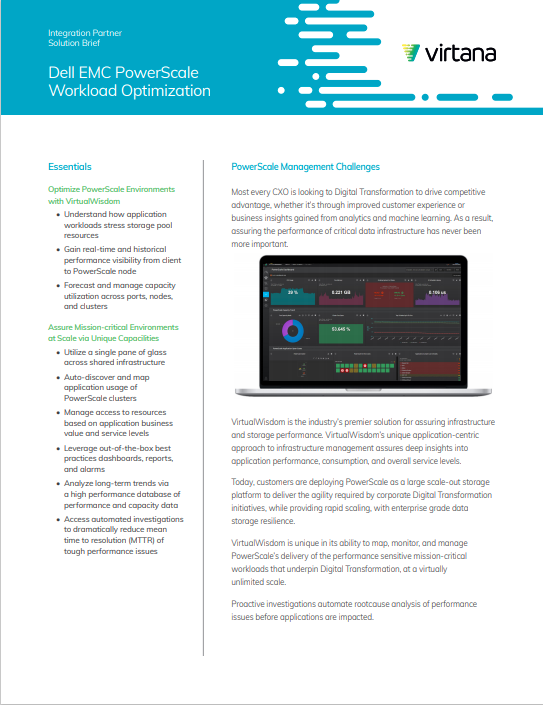
















0 Response to "42 isilon antivirus best practices"
Post a Comment