41 antivirus policy in cyber security
Cyber Security Policy - Betterteam The purpose of this policy is to (a) protect [ company name] data and infrastructure, (b) outline the protocols and guidelines that govern cyber security measures, (c) define the rules for company and personal use, and (d) list the company's disciplinary process for policy violations. Scope. Tech | Fox News News for Hardware, software, networking, and Internet media. Reporting on information technology, technology and business news.
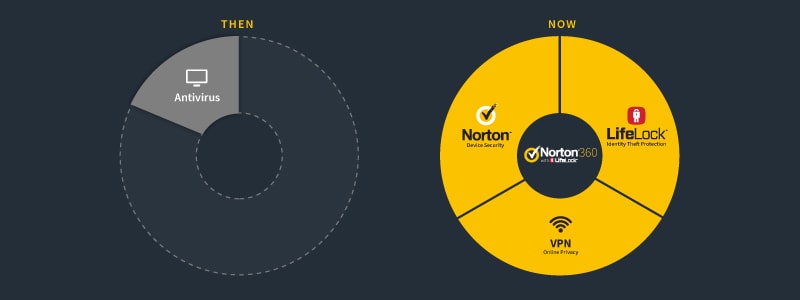
McAfee Antivirus Software 2022 Anti-Virus Free Download Beyond protection. Online protection beyond just antivirus . Adopting a more complete security solution goes beyond strictly PC antivirus. Protecting the expansive aspects of your digital life covers a wide spectrum of devices – including your PCs, Macs, iOS devices, and Android devices – all of which are key pillars supporting your connected lifestyle.
Antivirus policy in cyber security
Company cyber security policy template - Workable This Company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for setting up your employment policies. Policy brief & purpose Our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure. ITS Antivirus Policy - Loyola University Chicago Antivirus software helps protect computers from malicious code. Requiring antivirus software on certain operating systems will improve the overall security of Loyola's network. Policy: Use of antivirus software - All computers using the Loyola network may be required to use antivirus software depending on their operating system. Create a cyber protection policy for your small business using ... - Avast What's more, as most cyberattacks tend to exploit basic vulnerabilities in systems, they are easy to prevent with antivirus software, patch updating and staff awareness training. A cyber protection policy means your staff will be better informed and able to take appropriate action to prevent attacks Endpoint security
Antivirus policy in cyber security. All Medibank customers' personal data was compromised in the cyber ... All Medibank and ahm customers have been urged to contact the company's cyber response hotlines by phone (for ahm customers 13 42 46 and for Medibank customers 13 23 31) or through an information ... Difference between Antivirus and Internet Security - tutorialspoint.com Antivirus does not include firewall in its specifications. Internet Security does include firewall. Cost efficient. Antivirus software have both paid and free services, so they are comparatively cost efficient than Internet security. Internet Security is comparatively costlier as compared to Antivirus. Access. Antivirus and Malware Policy - Colorado Department of Education The purpose of this policy is to describe requirements for preventing and addressing computer virus, worm, spyware, malware, and other types of malicious software. Scope This policy applies to all [LEP] staff using [LEP] information resources. Policy The [Insert Appropriate Role] or their designee shall ensure: 5 Best Antivirus for Linux 2022 | Linux Antivirus - Comodo Why Comodo Free Antivirus for Linux OS? Comodo Antivirus for Linux is equally good as Comodo WindowsAntivirus. It performs cloud-based behavior analysis of files to deliver 360-degree protection against unknown and zero-day malware. It ensures proactive Linux Antivirus protection to stay ahead of all known and unknown threats.
A Guide to Writing an Effective Cybersecurity Policy it is expected that one company will become a victim of a ransomware attack every 14 seconds. Background information. Start your cybersecurity policy with reasons why it is created, for instance, to prevent unauthorized access or the misuse of the company's data. Policy's scope. Here, briefly describe the types of data records that will be ... #1 in Cloud Security & Endpoint Cybersecurity - Trend Micro Trend Micro is the global leader in enterprise cloud security, XDR, and cybersecurity platform solutions for businesses, data centres, cloud environments, networks, and endpoints. #1 in Cloud Security & Endpoint Cybersecurity | Trend Micro (SG) The Evolution of Antivirus to EDR & MDR | ConnectWise Learn more about antivirus & its evolution into next gen antivirus, endpoint detection & response, its role in the MITRE ATT&CK framework development and more! ... and manage client security policies and profiles Incident Response Service On-tap cyber experts to address critical security incidents Cybersecurity Glossary Guide to the most common ... Anti-Virus Policy - Information Services - University of Richmond - is Policy All computers that are connected to the University of Richmond network must have the standard supported anti-virus software installed and scheduled to run at regular intervals. In addition, the anti-virus software and the virus definition files must be kept up-to-date.
Cyber Security Policies - javatpoint This policy provides the following protection: It blocks the unauthorized users from accessing the systems and networks that connect to the Internet. It detects the attacks by cybercriminals. It removes the unwanted sources of network traffic. 3. Intrusion Prevention policy Cyber Security Policy - GeeksforGeeks Here are some cybersecurity policy covered in this article: 1. Acceptable Use of data Systems Policy The purpose of this policy is to stipulate the suitable use of computer devices at the corporate/company. These rules protect the authorized user and therefore the company also. Symantec Enterprise Cloud - Broadcom Inc. To meet today's Cyber Security challenges, enterprises need an integrated cyber defense platform that integrates industry-leading solutions and solves for the most pressing C-level challenges like evolving threats, privacy & compliance, and digital transformation. Top 25 free cyber security policy template - Cyber Hack Summary: · Malware Protection · Cybersecurity Policy: the Basics · Free Cyber Security Policy Template for Newbies and SMBs. 1. Password security; 2 ... Summary: This Company cyber security policy template is ready to tailor to your company's needs and can be a starting point for setting up your employment policies;
Manage antivirus settings with endpoint security policies in Microsoft ... Antivirus policy reports display status details about your endpoint security Antivirus policies and device status. These reports are available in the Endpoint security node of the Microsoft Endpoint Manager admin center. To view the reports, in the Microsoft Endpoint Manager admin center, go to Endpoint security and select Antivirus.
List of 25 antivirus policy in cyber security - Cyber Hack 11 Antivirus Policy and Procedure Best Practices - Security Program; 12 Anti-Virus and Anti-Malware - University of Regina; 13 Protect Your Device from Malware - Yale Cybersecurity; 14 Virus Protection and Patch Management Policy - San Mateo County; 15 ITS Antivirus Policy: Information Technology Services; 16 Anti-Virus Policy | Info ...
White House spotlights EV cybersecurity in climate push The White House cyber team on Monday gathered private sector leaders for a discussion focused on how secure electric vehicles will be key to achieving the Biden administration's climate goals ...
Create a cyber security policy for your business | CERT NZ For your customers, it means that your cyber security policy will: explain how you'll protect their data. This could mean making sure you encrypt their data, back up their data, and define how long you'll hold it for include making a security policy that's available for them to view — on your website, for example.
Cyber Security Policies And Standards | Learn eTutorials Security policies are defined as a set of high level rules that an organization issues by the high officials and security experts for all the employees of that organization who have access to the organization's sensitive information. It has the rules defining the way of accessing the information.
Cyber Awareness, Cyber Security and Anti-Virus Anti-virus is software that protects a computer from viruses and other threats. Cyber security is the protection of a computer system from hostile acts and criminals. It is important to be aware of the differences between these terms. Many people, including some in the government, still use the term 'cyber-security' instead of the more ...
Cyber Security Awareness Month: which VPN and antivirus to get The best antivirus to get this Cyber Security Awareness Month. We recommend Bitdefender as the best antivirus software, so if you need a new one, this could be the way to go. With 500 million ...
Cyber Security Security Policies and Procedures - The Law Office of ... Our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure. The more we rely on technology to collect, store and manage information, the more vulnerable we become to severe security breaches. ... installation of antivirus/anti-malware software. 3. KEEPING EMAILS ...
FAQs | PC Matic - The Leader in Cyber Security & Antivirus ... Make sure your cookie and security settings are correct - See our cookies and security FAQ pages for complete instructions. Use PC Matic's troubleshooting page - The suggestions there take into account any information we are able to gather from the system itself, so it often lets you zero in on specific problems quickly.
Email Security Policy ~ Crowley 4.1.1 Read and comply with this policy. 4.1.2 Protect the confidentiality, integrity, and availability of Company electronic information. 4.1.3 When contracting with an external IT supplier, help ensure the supplier meets contractual obligations to protect and manage Company IT assets. 4.2 Information Security
8 Essential Policies & Procedures for Improved Cyber Security Device Security. 7. Lost or Stolen Personal Device Procedure. 8. Social Media Security Policies. 1. Callback Procedures. This is by far one of the best things you can do to prevent cybercrime. We've all seen them - an email asking you to pay an invoice or change bank details from an apparent client or trusted individual.
Create a cyber protection policy for your small business using ... - Avast What's more, as most cyberattacks tend to exploit basic vulnerabilities in systems, they are easy to prevent with antivirus software, patch updating and staff awareness training. A cyber protection policy means your staff will be better informed and able to take appropriate action to prevent attacks Endpoint security
ITS Antivirus Policy - Loyola University Chicago Antivirus software helps protect computers from malicious code. Requiring antivirus software on certain operating systems will improve the overall security of Loyola's network. Policy: Use of antivirus software - All computers using the Loyola network may be required to use antivirus software depending on their operating system.
Company cyber security policy template - Workable This Company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for setting up your employment policies. Policy brief & purpose Our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure.


![Windows Defender Turned Off by Group Policy [Solved]](https://info.varonis.com/hubfs/Imported_Blog_Media/local-group-policy-editor-screenshot.png?hsLang=en)







![PDF] Cyber Security : Exploring Awareness among University ...](https://d3i71xaburhd42.cloudfront.net/b49f62de4dd6edafc0fae4deabf39404c5ce73c5/5-Table2-1.png)


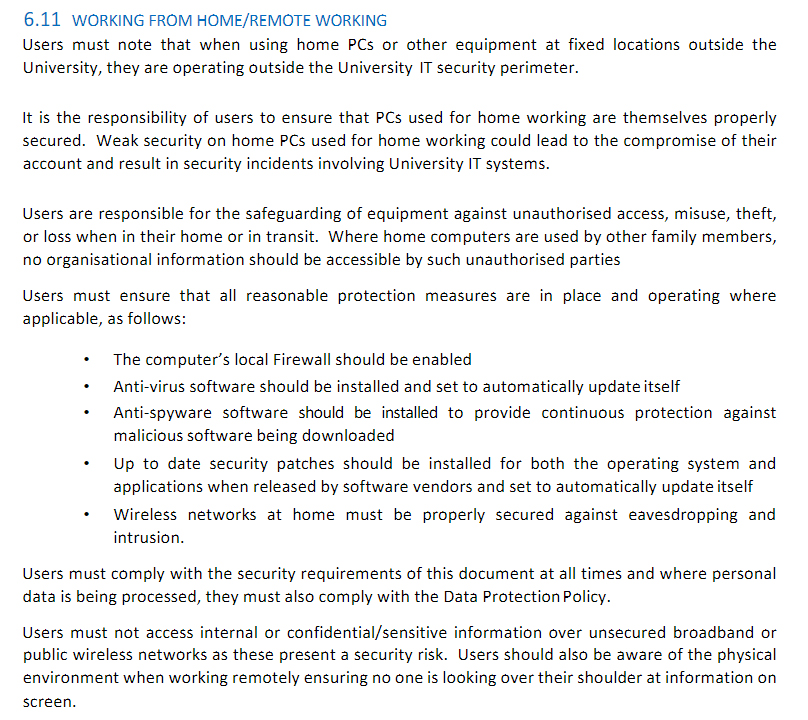

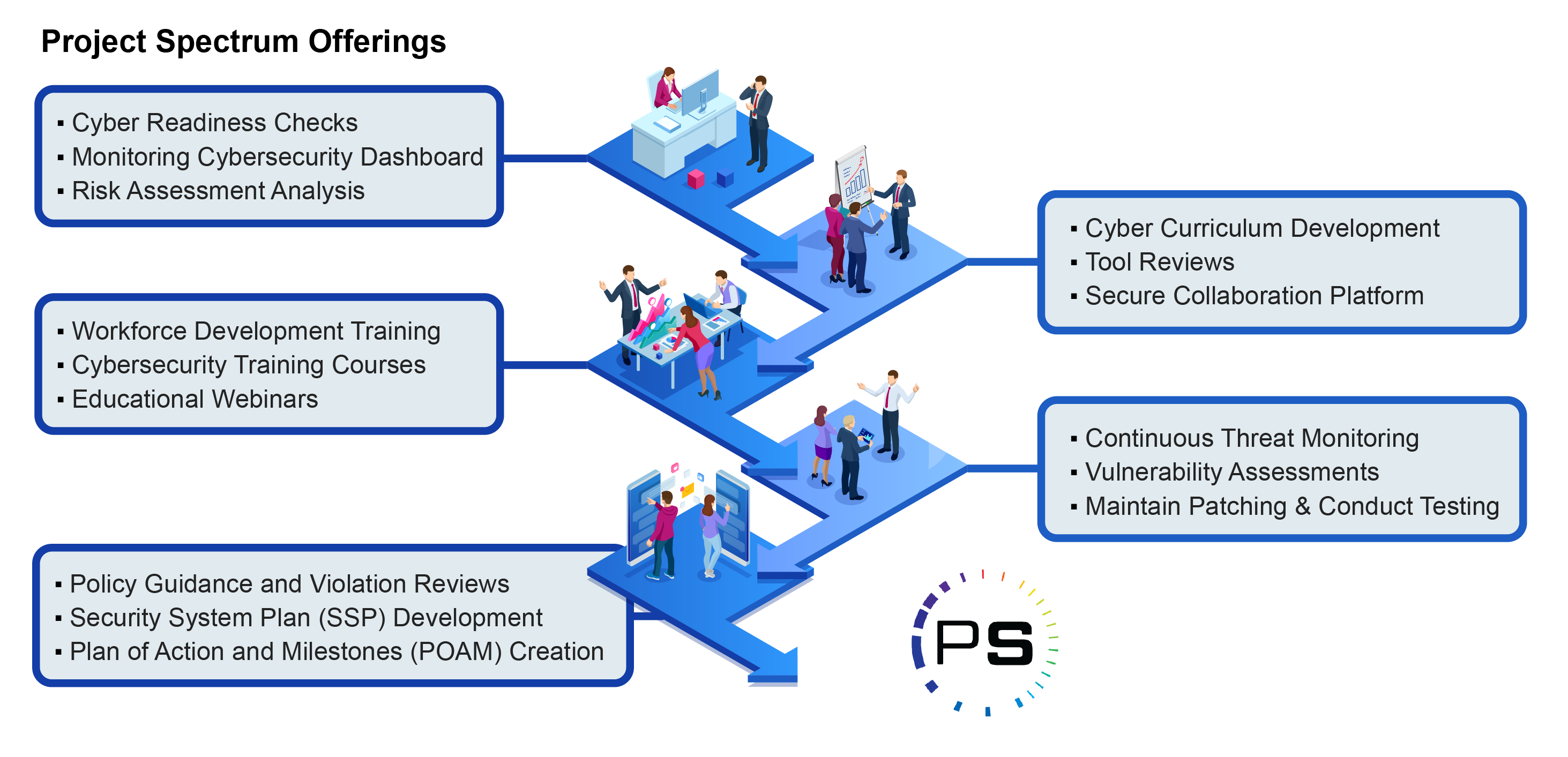
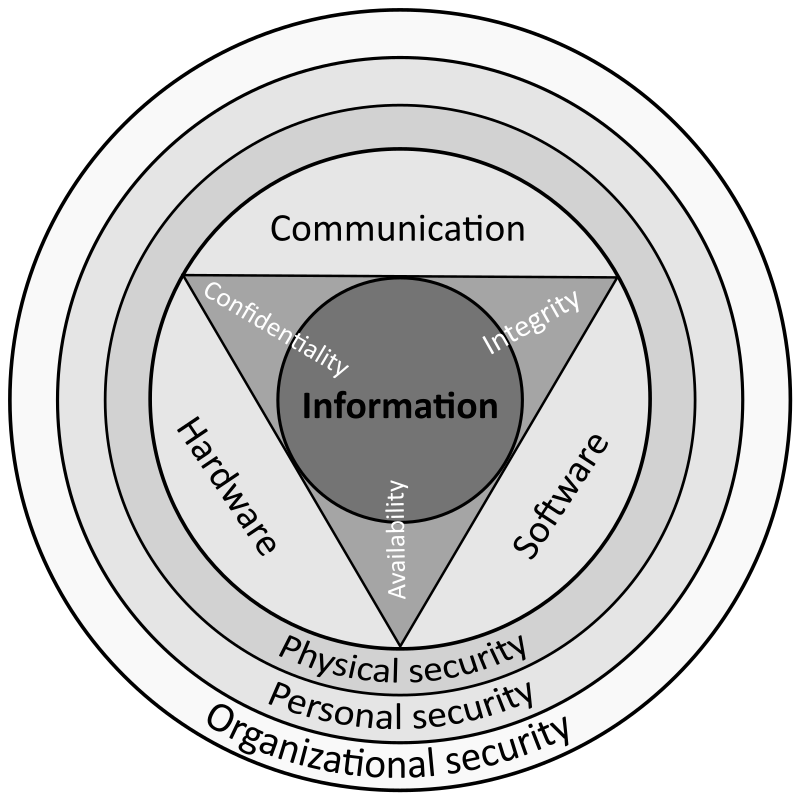


![42 Information Security Policy Templates [Cyber Security] ᐅ ...](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg)













0 Response to "41 antivirus policy in cyber security"
Post a Comment